Translated from:
CIA_vault7_MarbleFramework 反取证框架分析
CIA_vault7_MarbleFramework 反取证框架分析
0x0 The original information
0x1 Function
- The third in the wikileaks wave of leaked CIA documents, called “Marble,” contains 676 source code files from the anti-forensics Marble Framework and is basically a confusing tool used to hide the true source code of malicious CIA programs
- String/data obfuscation tools - algorithms designed to prevent forensic investigators and antivirus companies from tracing viruses, trojans, and hackers to the CIA
- Chinese, Russian, Korean, Arabic, Persian and other languages can also be implanted to disguise the identity of the attacker
0x2 The resources
https://wikileaks.org/ciav7p1/cms/space_15204359.html
https://wikileaks.org/ciav7p1/cms/files/Marble%20Framework.pptx
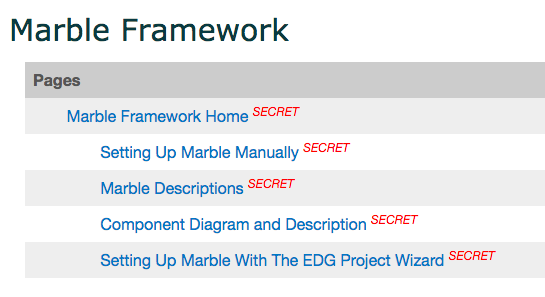
https://wikileaks.org/ciav7p1/cms/files/Marble%20Framework.pptx

0x3 The framework code
Framework USES VS tools, C++ language
0x31 The frame structure is as follows:
- Marble: A Marble is a specific algorithm that scrambles and unscrambles data.
- Mibster: The Mibster is the utility that does the scrambling and altering of source files. The Mibster starts by choosing a Marble (an algorithm) from the filtered list of available algroithms. The Mibster then scans the directories containing source, looking for an strings and data to scramble. The Mibster keeps a clean copy of the original source and replaces it with the scrambled versions of strings/data as well as supplies the unscramble function. The source should compile after Mibster modifies source.
- Mender: The Mender restores the source files to their original state. If, for any reason, the Mibster fails or breaks the code, the Meder can always restore the state to its original.
- Warble: A Warble is a wide-character string (wchar_t *) that needs to be scrambled by the Mibster.
- Carble: A Carble is a multi-byte string (char *) that needs to be scrambled by the Mibster.
- Validator: The Validator is a utility that takes (as an input) the receipt file generated by the Mibster. The Validator uses the receipt file to verify that all the strings intended to be scrambled are not contained in the final binary.
0x32 Implant language part, there are Unicode and UTF8 encoding
0x33 Framework code module tool
0x34 Mixed language
Either way, it’s a random implant
- Binary (CARBLE)

- Text string (WARBLE)
- Chinese means nothing
- Russian (but tested by Google as Mongolian, but still unable to translate)

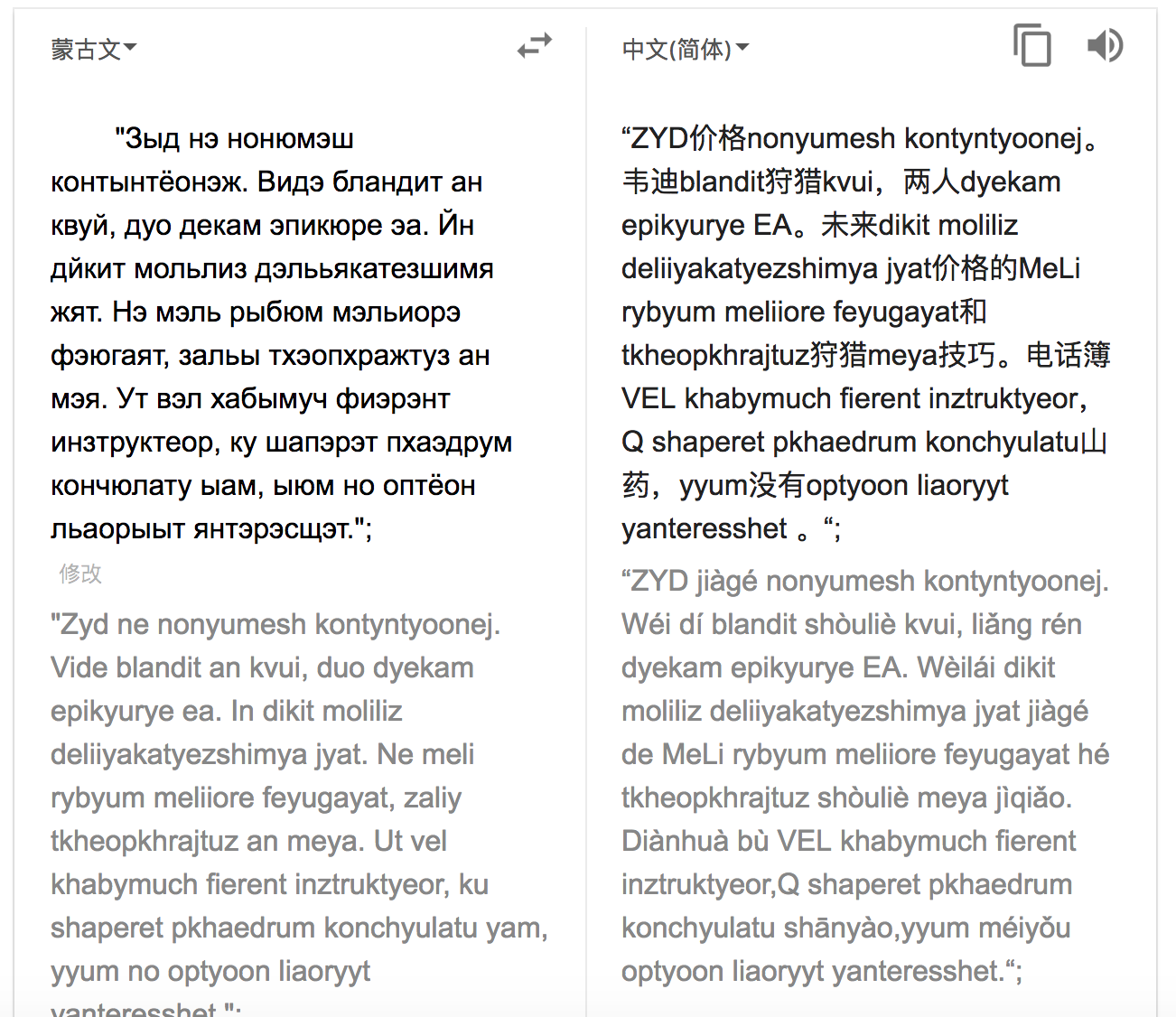
- Korean
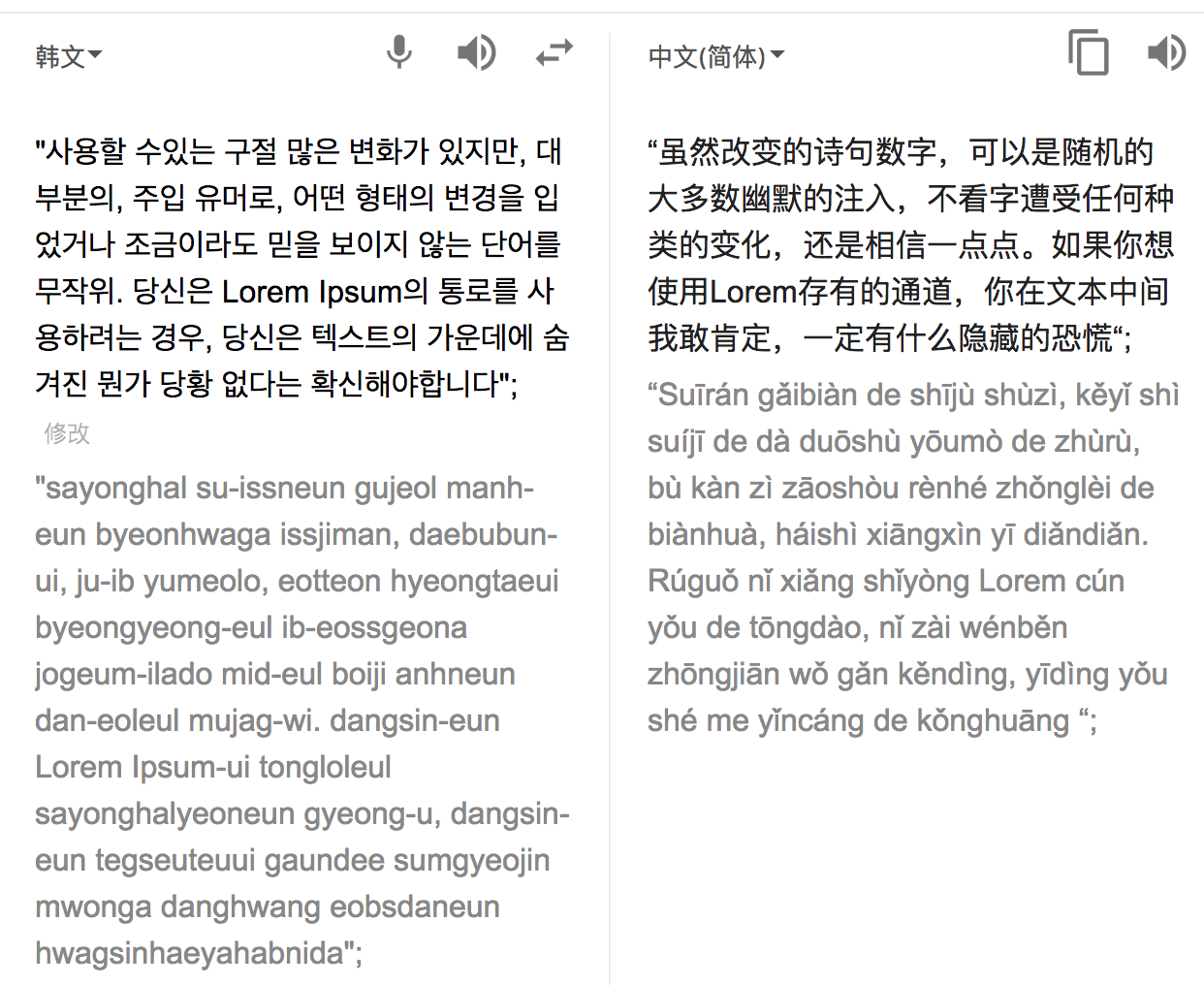
- Persian

0x4 Summary
Obfuscation tools are randomly implanted into texts of other languages to mislead analysts, but the semantics of texts currently used are unclear and the obfuscation effect is limited.
- Language misleads. I think it is more effective to replace key information with other languages, such as log output, return information and so on.
Moreover, for strict traceability technology, it needs to be judged based on a variety of factors. Marble alone is not enough to deceive experienced network forensics personnel.





没有评论:
发表评论